
Back معيار تعمية البيانات Arabic Verilənlərin şifrələnməsi standartı Azerbaijani DES BE-X-OLD DES Bulgarian DES Catalan Data Encryption Standard Czech Data Encryption Standard Danish Data Encryption Standard German Data Encryption Standard Greek DES (kriptado) Esperanto
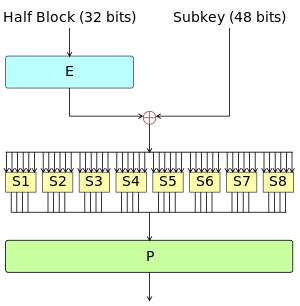 The Feistel function (F function) of DES | |
| General | |
|---|---|
| Designers | IBM |
| First published | 1975 (Federal Register) (standardized in January 1977) |
| Derived from | Lucifer |
| Successors | Triple DES, G-DES, DES-X, LOKI89, ICE |
| Cipher detail | |
| Key sizes | 56 bits |
| Block sizes | 64 bits |
| Structure | Balanced Feistel network |
| Rounds | 16 |
| Best public cryptanalysis | |
| DES has been considered unsecure right from the start because of the feasibility of brute-force attacks.[1] Such attacks have been demonstrated in practice (see EFF DES cracker) and are now available on the market as a service. As of 2008, the best analytical attack is linear cryptanalysis, which requires 243 known plaintexts and has a time complexity of 239–43 (Junod, 2001). | |
The Data Encryption Standard (DES /ˌdiːˌiːˈɛs, dɛz/) is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
Developed in the early 1970s at IBM and based on an earlier design by Horst Feistel, the algorithm was submitted to the National Bureau of Standards (NBS) following the agency's invitation to propose a candidate for the protection of sensitive, unclassified electronic government data. In 1976, after consultation with the National Security Agency (NSA), the NBS selected a slightly modified version (strengthened against differential cryptanalysis, but weakened against brute-force attacks), which was published as an official Federal Information Processing Standard (FIPS) for the United States in 1977.[2]
The publication of an NSA-approved encryption standard led to its quick international adoption and widespread academic scrutiny. Controversies arose from classified design elements, a relatively short key length of the symmetric-key block cipher design, and the involvement of the NSA, raising suspicions about a backdoor. The S-boxes that had prompted those suspicions were designed by the NSA to remove a backdoor they secretly knew (differential cryptanalysis). However, the NSA also ensured that the key size was drastically reduced so that they could break the cipher by brute force attack.[2] The intense academic scrutiny the algorithm received over time led to the modern understanding of block ciphers and their cryptanalysis.
DES is insecure due to the relatively short 56-bit key size. In January 1999, distributed.net and the Electronic Frontier Foundation collaborated to publicly break a DES key in 22 hours and 15 minutes (see § Chronology). There are also some analytical results which demonstrate theoretical weaknesses in the cipher, although they are infeasible in practice. The algorithm is believed to be practically secure in the form of Triple DES, although there are theoretical attacks. This cipher has been superseded by the Advanced Encryption Standard (AES). DES has been withdrawn as a standard by the National Institute of Standards and Technology.[3]
Some documents distinguish between the DES standard and its algorithm, referring to the algorithm as the DEA (Data Encryption Algorithm).